Alright, let me tell you about this whole “we tunnel” adventure we had a while back. It wasn’t some fancy pre-packaged thing, not at all. It was more like, we, as in me and a couple of buddies, had to figure out how to tunnel our way through some digital muck.
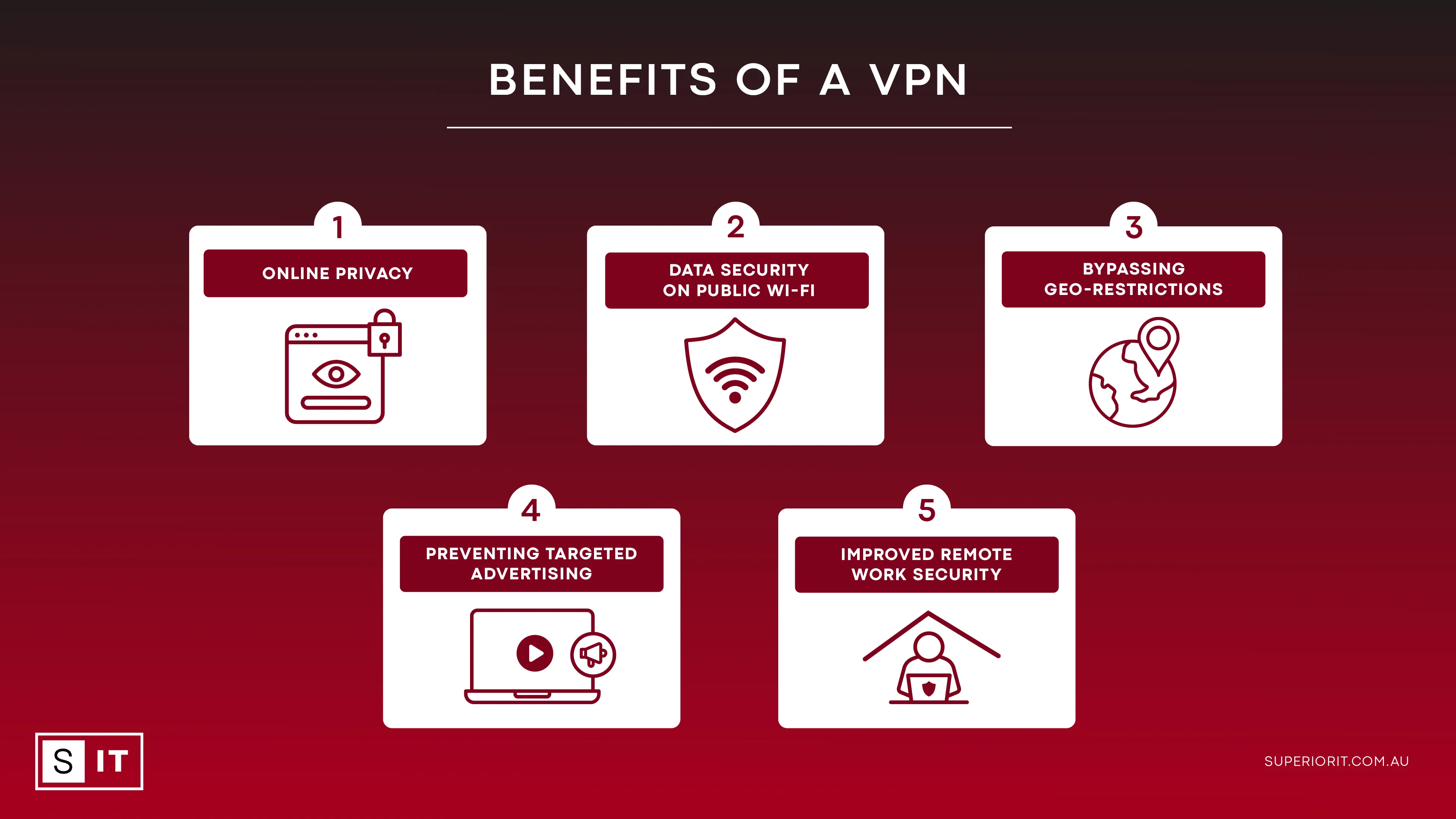
The Setup – Why We Even Bothered
So, picture this: we were trying to collaborate on this project, right? And the main server, the place with all our important stuff, was locked down tighter than a drum. Getting access from outside our usual spot was a nightmare. Official channels? Forget about it. Too much red tape, too slow, or they’d just say “nope, can’t do that for your specific, weird needs.” We needed a reliable, secure way to connect, to make it feel like we were all in the same room, even though we were miles apart. We needed to make sure our data wasn’t just floating out there for anyone to peek at. You know, keep our digital chit-chat private and our work safe from prying eyes.
The “Let’s Build a Tunnel” Phase
So, we decided, “Okay, let’s just build our own pathway.” That’s what “we tunnel” became for us – our little codename for this mission. We weren’t network gurus, not by a long shot. We started digging around, reading up on how these things work. You hear about these virtual private network things, how they create a sort of secret passage for your data. Sounds simple, right? Ha!
Our first few attempts were, let’s just say, comical. We tried a few different approaches:
- First try: We thought we could just use some basic tools we already had. That lasted about half a day before we realized it was like trying to plug a firehose with a thimble. Totally insecure and barely worked.
- Then came the “let’s follow an online guide” stage: Seemed promising. We found a few guides, picked one that looked doable. Spent a whole weekend fiddling with configurations, weird command lines, and trying to understand what an “encrypted handshake” even meant. More coffee was consumed than actual progress made, I swear.
- The “Is this even worth it?” moment: We hit a wall. Things wouldn’t connect, or if they did, it was slower than molasses in January. One of us was always messing up a setting, or a firewall on one end would just laugh at our attempts. Frustration levels were high. We almost threw in the towel.
The Breakthrough – Light at the End of Our Tunnel
But then, one late night, after way too much trial and error, something clicked. It was actually a tiny detail, some obscure setting we’d overlooked a dozen times. One of us spotted it, changed it, and boom! Connection established. Stable. And, as far as we could tell, secure. It felt like we’d struck gold. We actually cheered. It wasn’t pretty, the setup was probably a bit janky by professional standards, but it was our tunnel, and it worked!
So, What Did We Learn?
That whole “we tunnel” experience taught us a lot. More than just the technical bits, though. We learned that sometimes, if you want something done right for your specific needs, you gotta roll up your sleeves and figure it out yourselves, even if it’s a pain. It also made us realize how much we take easy, secure connections for granted when they just work.
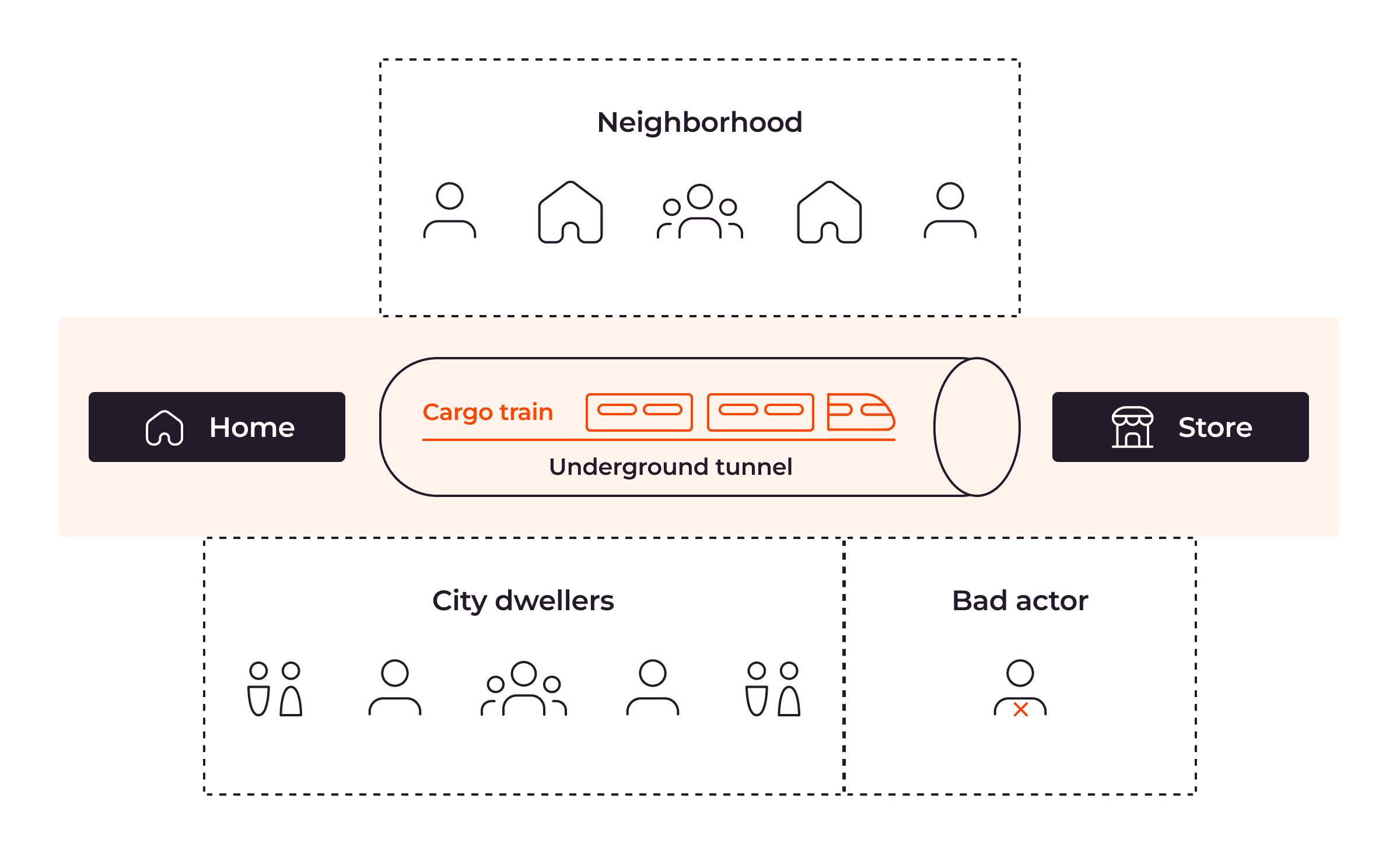
Looking back, the best part was that we did it together. We battled the tech, got annoyed, but ultimately figured it out as a team. And that little homemade tunnel? It kept our project going and our data safe, all because “we” decided to tunnel our way through the problem. It wasn’t about finding the perfect software; it was about making something work for us, by us. Sometimes, that’s the only way to get things done, especially when the “official” routes are just roadblocks.
